- info@datarecovery-sa.com
- Sat - Thu: 10.00 am - 10.00 pm
Ransomware Recovery
- Services
- Ransomware Recovery
Ransomware Recovery Services from Osool of integrated systems
Looking for professional Ransomware Recovery Services? At Osool Integrated Systems, we help businesses and individuals recover encrypted data quickly and securely. Our certified experts provide fast, effective ransomware removal and full data restoration — no matter the type of attack.
Ransomware attacks are a growing problem for computer users and server administrators. A lot of companies encrypted by ransomware in each of the past 5 years, and each instance of ransomware infection can big result in money of damages.
For years, we have recovered data for ransomware victims, but recently, we have begun to receive an influx of new cases. The threat will only grow, which is why datarecovery-sa.com now offers specialized services for ransomware recovery and decryption.
What is Ransomware?
Ransomware is a form of malicious software that encrypts your files, rendering them inaccessible until a ransom is paid to the attacker. These cyberattacks often target businesses, government institutions, and individuals, disrupting operations and causing massive data loss. Common types of ransomware include CryptoLocker, WannaCry, Locky, and Ryuk. Once infected, your systems may display a message demanding payment in cryptocurrency to restore access to your data.At Osool Integrated Systems, we strongly advise against paying the ransom, as it does not guarantee data recovery and may encourage further attacks. Instead, trust our certified experts to safely and effectively recover your encrypted files.How Our Ransomware Recovery Process Works
Our ransomware recovery process is built on a systematic and secure approach to ensure the maximum chance of data retrieval without risking further damage to your systems. Here’s how we do it:- Initial Assessment: We begin with a full diagnostic to identify the ransomware strain and assess the extent of the damage.
- System Isolation: We isolate infected systems to prevent the spread of the malware across your network.
- Ransomware Decryption: Our team uses advanced tools, proprietary scripts, and a growing database of ransomware keys to decrypt your files whenever possible.
- Data Recovery: If decryption isn’t possible, we attempt recovery using file system techniques, backups, and shadow copies (if available).
- Malware Removal: We clean your systems from any remaining threats to prevent re-infection.
- System Hardening: We provide guidance and implement security improvements to protect your infrastructure against future attacks.
Why Choose Osool for Ransomware Data Recovery?
- Fast turnaround time: We act quickly because every minute matters when your business is down.
- High recovery success rate: Our team has helped dozens of businesses restore critical data after ransomware attacks.
- Confidential and secure handling: We understand the sensitivity of your data and ensure complete confidentiality throughout the process.
- No recovery, no charge: You only pay if we successfully recover your data. No hidden fees.
- 24/7 Support: Ransomware can strike anytime — our emergency team is ready to help, day or night.
Ready to Recover Your Data?
If you’ve been hit by a ransomware attack, don’t panic. Contact the experts at Osool Integrated Systems for a free consultation and immediate support. We’ll guide you through every step of the recovery process with transparency, professionalism, and results.Our ransomware removal experts follow industry best practices to remove malware and ransomware without risking further damage to your systems.📞 Call us: +966 53 101 0903📧 Email: info@datarecovery-sa.comOr click the button below to start your case now.Start Your Case
You need fast access to your files, but immediately paying the ransomware creator is not a safe or effective option. Call us +966 53 101 0903 today to speak with a malware expert or read on to understand your options.
How is Ransomware Installed On My Computer?
How is Ransomware Installed on My Computer?
Ransomware usually enters the system when you open an infected file
(such as an .exe or a document containing macros).
Avoid opening any untrusted files — especially if the source is unknown.
Below is a list of common ransom note file names that may appear after infection.
Click a file name to copy it to clipboard
⚠️ Warning: If you suspect you have a ransomware-infected file, do not open it.
Disconnect the device from the network and contact professionals for safe data recovery.
The good news is that some ransomware programs use outdated encryption, some of the encryption techniques have been broken, and some keys and source code have been recovered (often after the creator is arrested) enabling decryption. However, in many cases, ransomware encryption is unbreakable.
If your computer is infected with ransomware, Osool of integrated systems can help you restore the affected data. As one of the world’s top data recovery companies, we can assist malware victims in several ways:
- Determine Recoverability – In many instances, data is recoverable via an alternative method. Our engineers will assess your unique situation to determine the safest and most cost-effective option for restoring your important files.
- Data Decryption – We can determine whether a decryption key exists for your ransomware infection or if one can be created. If decryption is feasible, we can perform the process safely, returning your systems to a functional state.
As every case is different, we cannot guarantee that a decryption method exists for your case without performing an evaluation.
Call us at +966 53 101 0903 and ask to speak with a ransomware recovery specialist.
Types of Ransomware and Data Recovery Options
Ransomware (or cryptovirus) is a malicious program that blocks access to data by encrypting the victim’s media.
It then demands money (usually via Bitcoin) to unlock the files. Unless the ransom is paid, the data remains permanently encrypted.
Examples of Ransomware:
- SamSam
- Cerber
- Crysis
- CrypMIC
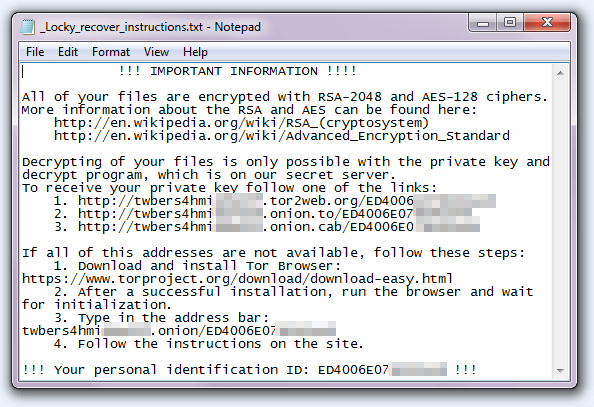
- Locky
- HDDCryptor
- Merry X-Mas
- CryptXXX
- CryptoWall
- CryptoLocker
- TorrentLocker
- KeRanger
- Bart
- Zepto
- Jigsaw
The good news: some ransomware uses outdated encryption or leaked keys, which makes decryption possible.
However, many modern ransomware strains use strong encryption that cannot be broken without the right key.
How Osool Integrated Systems Can Help
- Determine Recoverability: Our engineers assess your case to see if data can be restored using alternative methods.
- Data Decryption: We check if decryption keys exist for your ransomware type, or if a custom solution is possible.
- Safe Recovery: If decryption isn’t available, we attempt recovery using advanced techniques without further damage.
Note: Every case is unique, and we can’t guarantee decryption without first performing an evaluation.
📞 Call us: +966 53 101 0903
📧 Email: info@datarecovery-sa.com
📧 Email: info@datarecovery-sa.com